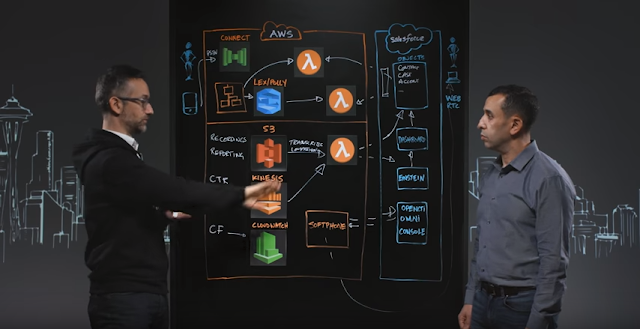
How to get your Data to AWS

Bring On The Data Whether you are dealing with a single massive database, millions of log files or stream of data from thousands of IoT sensors the data AWS offers services that can be combined to facilitate the secure and efficient transport of your data to the cloud. This article will provide an overview of how to handle the three common data sources: files, databases and data streams. How to Handle Files The simplest way to get files into AWS is to upload them to AWS Simple Storage Service (S3) . S3 supports multi-part uploads of 5 GB chunks to form a single file with a maximum size of 5 TB. By default, S3 uses the Internet to transport the data, therefore if you are transporting sensitive information be sure to use AWS Key Management Service (KMS) to perform client-side and server-side data encryption. If you are frequently moving Terabytes of data, AWS Direct Connect provides a private, dedicated, 1Gbps or 10Gbps consistent network connection betw